Table of Contents
Table of Contents
In the dynamic realm of computer networks, maintaining optimal performance and security is paramount. Whether you're an IT professional, a network administrator, or simply a curious enthusiast, understanding the types of network monitoring tools available to you can make a world of difference.
Just like superheroes safeguarding a city, network monitoring tools play a crucial role in monitoring, managing, and protecting the intricate web of connections that keep our digital world thriving. These tools empower us to keep a watchful eye on network performance, detect anomalies, troubleshoot issues, and fortify security defences.
In this comprehensive guide, we will embark on a thrilling journey through the vast landscape of network monitoring tools. From the familiar stalwarts to the lesser-known gems, we'll explore an array of tools that form the arsenal of network professionals. Get ready to meet the superheroes of network monitoring!
Before we get too far into the different types of network monitoring, let’s all make sure we’re on the same page about what network monitoring actually is.
Network monitoring refers to the practice of monitoring computer networks, both local area networks (LANs) and wide area networks (WANs), to ensure their smooth operation, performance, and security. It involves the continuous surveillance and analysis of network components, such as routers, switches, servers, and other network devices, to gather data and detect any abnormalities or issues.
The primary goal of network monitoring is to maintain the optimal functioning of a network infrastructure by proactively identifying and resolving problems, minimizing downtime, and maximizing performance. It provides administrators and IT professionals with real-time visibility into network traffic, bandwidth utilization, network utilization, device health, and security threats.
Network monitoring tools and software are used to collect and analyze network data, including network traffic, bandwidth usage, latency, packet loss, error rates, and device statistics. These tools provide valuable insights into network performance metrics, allowing administrators to identify bottlenecks, troubleshoot issues, and optimize network resources.
Network monitoring tools are specifically designed to oversee, control, and uphold the performance, accessibility, and overall well-being of computer networks. These software solutions engage in ongoing monitoring and analysis of network devices, including servers, routers, switches, firewalls, and other hardware components, as well as network services and applications.
By gathering and scrutinizing data concerning diverse network parameters like response times, bandwidth utilization, and error rates, network monitoring tools have the capacity to pinpoint potential problems, bottlenecks, or outages. Administrators are promptly alerted through real-time notifications and alerts provided by these tools whenever performance issues or security threats are detected, enabling swift troubleshooting and resolution.
Looking to solve your network issues and get complete network visibility? Unlock valuable insights into your network's performance with Obkio's end-to-end network monitoring solution today. Don't let any missing pieces hold you back -
And see the full picture of your network's performance.

- 14-day free trial of all premium features
- Deploy in just 10 minutes
- Monitor performance in all key network locations
- Measure real-time network metrics
- Identify and troubleshoot live network problems

While there are various types of network monitoring tools available in the market, they often share common key features that enhance their effectiveness. These features provide administrators with essential capabilities for monitoring, managing, and securing computer networks. Whether you opt for a specific type of network monitoring tool or a comprehensive solution, you can expect to find these core features embedded across most options.
In this section, we will explore these fundamental features that form the backbone of network monitoring tools, enabling administrators to gain real-time visibility, identify issues, optimize performance, and ensure network security. Let's delve into these key features that transcend the boundaries of different network monitoring tool types, equipping administrators with powerful monitoring capabilities.
- Real-time monitoring: Network monitoring tools provide real-time visibility into network performance, allowing administrators to monitor network devices, traffic, and services as they happen. This feature enables prompt identification of issues and immediate response.
- Device and interface monitoring: These tools track the health and status of network devices, such as routers, switches, servers, and firewalls. They monitor key metrics like CPU and memory utilization, interface status, and error rates, providing insights into the overall health of the network infrastructure.
- Bandwidth monitoring: Network monitoring tools measure and analyze bandwidth usage across the network. They help monitor network bandwidth, identify bandwidth-intensive applications, detect potential bottlenecks, and ensure efficient resource allocation.
- Performance metrics and analytics: These tools gather and analyze performance metrics such as latency, packet loss, and network response times. By visualizing these metrics, administrators can identify performance issues, troubleshoot network slowdowns, and optimize network performance.
- Alerts and notifications: Network monitoring tools generate alerts and notifications based on predefined thresholds or anomalies. Administrators receive immediate notifications via email, SMS, or dashboard alerts when network devices or services experience performance degradation, downtime, or security threats.
- Network mapping and visualization: Network monitoring tools provide graphical representations of the network infrastructure, displaying device connectivity, topology, and network traffic flows. Network visualization assists administrators in understanding the network layout and identifying potential points of failure.
- Security monitoring: Many network monitoring tools include security-focused features such as intrusion detection and prevention systems (IDS/IPS), firewall monitoring, and anomaly detection. These features help identify and mitigate potential security breaches, unauthorized access attempts, and malicious activities.
- Reporting and analytics: Network monitoring tools generate detailed reports and analytics on network performance, availability, and security. These reports provide historical data, trends, and insights that assist administrators in making informed decisions regarding network optimization, capacity planning, and security enhancements.
- Remote monitoring and management: Network monitoring tools often support remote access, allowing administrators to monitor and manage networks from anywhere. This feature is especially beneficial for distributed or remote networks, enabling efficient troubleshooting and management.
By leveraging these key features, network monitoring tools empower administrators to proactively monitor, manage, and secure their networks, ensuring optimal performance, reliability, and security.

There are different types of network monitoring tools because networks vary in size, complexity, and specific monitoring needs. Different types of networks, such as local area networks (LANs), wide area networks (WANs), data centers, cloud environments, or virtualized networks, may require specialized monitoring tools to address their unique characteristics and challenges.
Additionally, network monitoring tools cater to diverse monitoring objectives. Some tools focus on network performance monitoring, and tracking metrics like bandwidth utilization, latency, packet loss, and response times. Others specialize in network security monitoring, detecting and mitigating security threats, intrusion attempts, or abnormal network behaviour. There are also tools designed for application monitoring, protocol analysis, log monitoring, and more.
Furthermore, network monitoring tools vary in terms of their features, scalability, integration capabilities, and deployment options. Some tools may offer comprehensive, all-in-one solutions, while others provide more specific functionalities and may require integration with complementary tools to achieve a complete monitoring setup.
The diverse types of network monitoring tools cater to the specific requirements of different networks and monitoring objectives. They allow administrators to tailor their monitoring approach to their network's characteristics, goals, and constraints. By choosing the appropriate tools, administrators can effectively monitor, manage, and secure their networks while optimizing performance and minimizing downtime.

If you want to skip to a certain Network Monitoring tool, you can do so now:
- Passive Network Monitoring Tools
- Active Network Monitoring Tools
- Network Performance Monitoring Tools
- Network Device Monitoring Tools
- Synthetic Network Monitoring Tools
- SNMP Network Monitoring Tools
- Cloud Network Monitoring Tools
- Flow-Based Network Monitoring Tools
- Distributed Network Monitoring Tools
- Remote Network Monitoring Tools
- Application Performance Monitoring Tools
- Network Packet Monitoring Software
- Network Traffic Monitoring Software
- Network Security Monitoring Tools
Passive network monitoring refers to the practice of monitoring network traffic without actively participating in the network's communication process. It involves capturing and analyzing network packets as they traverse the network, without interfering with or modifying the traffic flow.
In passive monitoring, a network monitoring tool or system is connected to a network segment or a network tap, allowing it to passively observe and capture network packets. The tool collects these packets and analyzes their content, extracting valuable information about network performance, security, and application behaviour.
The primary advantage of passive network monitoring is that it provides an unobtrusive and non-invasive method of monitoring. It does not introduce additional network traffic or latency since it operates by simply observing the existing network traffic.
Passive network monitoring offers a range of key features that contribute to its effectiveness in monitoring and analyzing network traffic. Here are some key features of passive network monitoring:
- Traffic capture: Passive monitoring tools capture network traffic by deploying sensors or network probes at strategic points within the network infrastructure. These tools intercept and copy network packets without interrupting or altering the flow of traffic, allowing for non-intrusive monitoring.
- Real-time and historical analysis: Passive monitoring tools enable real-time analysis of network traffic, allowing administrators to monitor and react to events as they occur. Additionally, captured traffic data can be stored for historical analysis, facilitating the identification of patterns, trends, and long-term performance evaluation.
- Protocol and application analysis: Passive monitoring tools often include protocol decoders and application-aware analysis capabilities. They can interpret and analyze various network protocols and applications, providing detailed insights into application performance, traffic patterns, and behaviour.
- Performance metrics and statistics: Passive monitoring solutions extract performance metrics and network statistics from captured network packets. These metrics can include bandwidth utilization, packet loss, latency, response times, traffic volumes, and application-specific metrics. By analyzing these metrics, administrators can identify performance bottlenecks, network congestion, or anomalies affecting network performance.
- Anomaly and threat detection: Passive monitoring tools can identify anomalous network behaviour or security threats by comparing observed traffic patterns against a baseline or predefined profiles. This helps in detecting network intrusions, malware infections, distributed denial-of-service (DDoS) attacks, or suspicious activities that may indicate potential security breaches.
- Traffic filtering and categorization: Passive monitoring solutions often provide traffic filtering capabilities, allowing administrators to focus on specific types of traffic or protocols of interest. They can filter traffic based on source/destination IP addresses, port numbers, protocols, or specific application signatures, facilitating targeted analysis and troubleshooting.
Passive network monitoring tools are valuable in various use cases where businesses need to gain insights into network traffic and performance without actively generating traffic or disrupting the network.
Certainly, here are a few specific use cases for passive network monitoring tools:
Network Anomaly Detection:
Passive network monitoring tools can be used to detect unusual traffic patterns and anomalies that may indicate security threats, such as Distributed Denial of Service (DDoS) attacks, network scanning, or unauthorized access attempts. Since they don't actively interact with the network, they can quietly analyze traffic for suspicious behavior.
Application Performance Analysis:
Passive monitoring tools can help assess the performance of critical applications by analyzing network traffic related to those applications. This includes measuring response times, identifying latency issues, and determining the impact of network congestion on application performance.
Forensic Analysis:
In the event of a security incident or data breach, passive network monitoring tools capture detailed network traffic data that can be invaluable for forensic analysis. They provide a historical record of network activity, helping investigators reconstruct the sequence of events and identify the source and scope of the breach.
Compliance and Data Retention:
Passive monitoring is often used to maintain compliance with data retention requirements imposed by regulations. It enables businesses to archive network traffic data for auditing and reporting purposes, which may be necessary for demonstrating compliance with data protection laws or industry-specific regulations.
Traffic Prioritization and QoS Monitoring:
Passive monitoring tools can help businesses maintain the quality of service by monitoring traffic and ensuring that network resources are allocated according to established priorities and QoS policies. They can identify if important applications are receiving the necessary bandwidth and resources.
Active network monitoring refers to the practice of actively generating network traffic or sending specific test packets to evaluate and measure network performance, availability, and responsiveness. Unlike passive network monitoring, which observes existing network traffic, active monitoring involves proactive and deliberate network testing.
In active monitoring, specialized tools or systems generate synthetic network traffic, often referred to as probes or test packets, and send them across the network infrastructure. These test packets simulate typical network interactions and measure various performance metrics, such as response times, latency, packet loss, and throughput. The results are then analyzed to assess network performance and detect any issues or abnormalities.
Active network monitoring typically involves:
- Deploying monitoring agents or probes in key network locations for end-to-end monitoring.
- The agents or probes continuously send synthetic data packets across the network to measure network latency, throughput, and packet loss.
- These tools also allow network administrators to simulate user behaviour and test how the network responds under different loads and conditions.
Active network monitoring complements passive monitoring by providing proactive and targeted insights into network performance. It enables administrators to actively test network behaviour, detect issues in real-time, and take proactive measures to optimize network performance and ensure reliable network connectivity.
Because Active network monitoring tools are distributed in nature and can monitor modern decentralized network architectures, they increasingly replacing older Passive network monitoring solutions.
Active network monitoring encompasses various features that contribute to its effectiveness in assessing and managing network performance. Key features of active network monitoring include:
- Proactive testing: Active network monitoring involves the proactive generation of test traffic or probes to evaluate network performance. This feature allows administrators to actively simulate network interactions and measure performance metrics, such as latency, response times, packet loss, and throughput.
- Multiple test types: Active monitoring supports different types of tests to evaluate various aspects of network performance. Common test types include ping tests, HTTP/HTTPS tests, DNS tests, traceroutes, and synthetic transactions. This variety enables administrators to assess different network layers, services, and protocols.
- Test result analysis and reporting: Active monitoring tools provide comprehensive analysis and reporting capabilities. They collect and analyze test results, generate performance reports, and present visual representations of data trends. This allows administrators to gain insights into network performance, identify patterns, and make data-driven decisions for optimization and troubleshooting.
- Threshold monitoring and alerts: Active monitoring tools enable administrators to define thresholds for performance metrics. When performance metrics exceed or fall below these thresholds, alerts or notifications are generated. This feature ensures timely awareness of network performance issues and facilitates proactive actions to mitigate potential problems.
- Historical data storage and trend analysis: Active monitoring solutions typically store historical data, enabling trend analysis and long-term performance evaluation. Administrators can review historical performance data, compare current performance with past trends, and identify performance patterns or recurring issues over time.
- Scalability and distributed testing: Active monitoring tools can scale to accommodate large network environments and distributed infrastructures. They support distributed testing, allowing administrators to conduct tests from multiple locations or network segments simultaneously. This capability is particularly valuable for organizations with geographically dispersed networks.
Obkio Network Performance Monitoring tool is a simple cloud-based active Network Monitoring tool designed to monitor end-to-end network performance from the end user perspective, and to fulfil the need within the industry for a solution that simplifies network monitoring for all network types. Obkio leverages Network Monitoring Agents and synthetic traffic to continuously identify the causes of intermittent VoIP, video, and applications slowdown in seconds - and identify the data you need to troubleshoot and ultimately improve the end-user experience.

Active network monitoring tools are designed to actively generate traffic and test the network's performance, availability, and responsiveness. They are typically used in situations where you want to proactively assess the network's capabilities and identify potential issues.
Network Performance Testing:
Active monitoring tools are valuable for evaluating the network's performance under different conditions. For instance, businesses can generate synthetic traffic to measure network latency, jitter, packet loss, and throughput to ensure the network meets performance requirements.
Service-Level Agreement (SLA) Verification:
When businesses rely on third-party service providers or cloud services, active monitoring tools can be used to verify that service providers are meeting the terms of their SLAs. By actively testing service availability and performance, organizations can hold service providers accountable.
Load Testing and Scalability Assessment:
Active monitoring tools are useful for conducting load tests to assess how the network and applications perform under heavy traffic loads. This helps in determining the network's scalability and identifying potential bottlenecks before they impact users.
Network Failover Testing:
Active monitoring tools can be used to simulate network failures and test the effectiveness of network failover mechanisms. This is important for ensuring high availability and disaster recovery preparedness.
Change Management:
When making changes to the network infrastructure, such as adding new devices, altering configurations, or implementing security measures, active monitoring tools can be used to assess the impact of these changes on network performance. By proactively testing, organizations can identify and address issues before they affect users.
Service Quality Testing:
Active monitoring tools can simulate the use of specific applications or services to assess their quality and performance. For example, organizations can use active monitoring to verify VoIP call quality, video conferencing performance, or the responsiveness of web applications.
Network Redundancy Testing:
To ensure network redundancy and failover mechanisms are functioning as expected, businesses can use active monitoring tools to test failover scenarios. This helps verify that network redundancy is effective in maintaining service availability.
Security Vulnerability Testing:
Active monitoring tools can be used to simulate common security threats and vulnerabilities, such as port scanning or vulnerability scanning, to assess the network's ability to detect and respond to security risks.
End-to-End Connectivity Testing:
Active monitoring tools can perform end-to-end connectivity tests to ensure that all devices and network segments are functioning as expected. This helps in identifying and resolving connectivity issues proactively.
User Experience Assessment:
Active monitoring tools can assess the user experience by simulating user interactions with applications, websites, or services. This allows organizations to gauge the performance of these services from the user's perspective.
Confidently navigate the network monitoring tools landscape with our ultimate buyer's guide. Expert insights, use cases, and tips for informed choice
Learn more

Network Performance Monitoring or NPM is a more specific type of Network Monitoring. It is the process of monitoring end-to-end network performance and end-user experience to optimize network performance and troubleshoot network issues. Unlike traditional monitoring, network performance monitoring measures network performance from the end-user perspective, between two points in the network.
For Example:
- The performance of a user, who works in the office, and the application they use in the company’s data center
- The performance between two offices in a network
- The performance between the head office and the Internet
- The performance between your users and the cloud
Network performance monitoring ensures that the network is operating efficiently and effectively and identifies and addresses network availability issues and network performance issues anywhere in your network infrastructure. This process involves collecting information about network traffic, bandwidth usage, packet loss, latency, and other key network metrics, as well as using various tools and techniques to analyze and interpret this data.
The performance data gathered through network performance monitoring can be used to set or raise network performance expectations, troubleshoot and help fix network issues, and make informed decisions about network capacity and infrastructure priorities and planning.

Network performance monitoring provides critical insights and tools to optimize network performance, ensure SLA compliance, troubleshoot issues efficiently, and enhance the user experience. It empowers administrators with data-driven decision-making capabilities, leading to a more reliable and efficient network infrastructure.
- Proactive issue detection: Network performance monitoring enables the early detection of performance issues and anomalies in the network. By continuously monitoring network metrics such as latency, packet loss, and bandwidth utilization, administrators can identify potential bottlenecks or degradation in real-time, allowing them to take proactive measures before users are affected.
- Performance optimization: By analyzing network performance data, administrators can identify areas for optimization and improvement. They can identify network segments or devices that are experiencing high latency or congestion, allowing them to take corrective actions such as adjusting network configurations, optimizing routing paths, or upgrading network components to enhance overall performance.
- SLA compliance: Network performance monitoring enables organizations to monitor and enforce service level agreements (SLAs) with network service providers. By tracking key performance indicators (KPIs) outlined in service or Internet SLAs, administrators can ensure that service providers meet their contractual obligations and take appropriate actions if SLAs are not being met.
- Troubleshooting and root cause analysis: When network issues occur, performance monitoring provides valuable insights for troubleshooting and root cause analysis. By examining performance metrics, administrators can pinpoint the source of the problem, whether it's a misconfiguration, faulty hardware, or network congestion. This speeds up the troubleshooting process and facilitates faster resolution.
- Vendor management and optimization: Network performance monitoring helps organizations evaluate and optimize their relationships with network vendors. By tracking performance metrics, administrators can compare the performance of different vendors and make informed decisions about vendor selection, contract renewals, or negotiations for improved service quality.
- User experience improvement: Network performance directly impacts user experience, especially for applications that rely heavily on network connectivity. By monitoring performance metrics, administrators can ensure optimal user experience by identifying and resolving performance issues promptly. This leads to improved productivity, user satisfaction, and customer retention.
- Historical analysis and reporting: Network performance monitoring tools often store historical data, allowing administrators to perform trend analysis, generate reports, and track performance over time. This historical perspective helps identify patterns, detect recurring issues, and assess the effectiveness of performance optimization efforts.
Obkio is a cloud-based network performance monitoring and testing tool that helps organizations monitor the performance of their network infrastructure and applications. With Obkio, IT pros can monitor network metrics, including latency, packet loss, and network jitter, and troubleshoot network issues in real-time to ensure optimal network performance.
Network performance monitoring tools are essential for maintaining and optimizing the performance of a business's network infrastructure. Here are a few specific instances or use cases when businesses should use network performance monitoring tools:
Performance Baseline Establishment:
Before making any changes or updates to the network, businesses should use network performance monitoring tools to establish a performance baseline. This baseline provides a clear picture of normal network performance, which is invaluable for detecting deviations or issues in the future.
Network Troubleshooting:
When users experience slow connectivity, application performance issues, or other network-related problems, performance monitoring tools can help identify the root causes. They allow IT teams to pinpoint bottlenecks, congestion points, or configuration errors that may be impacting network performance.
Capacity Planning:
Network performance monitoring tools assist in network capacity planning by tracking resource utilization, bandwidth usage, and traffic patterns. This information is crucial for determining when and where network upgrades or optimizations are needed to accommodate growing demands.
Application Performance Optimization:
These tools can be used to assess the performance of critical applications running on the network. By monitoring the application response times and user experience, businesses can optimize application performance to ensure that they meet service level agreements (SLAs).
User Experience Enhancement:
Businesses can use network performance monitoring tools to ensure a positive user experience by identifying and resolving performance issues that may be affecting end users. This is particularly important for businesses that rely on web applications or online services.
Quality of Service (QoS) Management:
For organizations that prioritize certain types of traffic (e.g., voice or video traffic), network performance monitoring tools help monitor and manage QoS parameters to ensure that critical traffic receives the necessary resources and low-latency treatment.
Change Management:
Whenever changes are made to the network, such as adding new devices, updating configurations, or implementing new security policies, network performance monitoring tools help assess the impact of these changes on network performance. This proactive approach helps prevent performance issues from arising after changes are implemented.
Remote Office/Branch Office (ROBO) Monitoring:
For businesses with multiple remote or branch offices, network performance monitoring tools can ensure that these locations have consistent access to central resources and services. They help identify and resolve performance issues at remote sites.
Vendor and Service Provider Accountability:
Businesses can use network performance monitoring tools to monitor and measure the performance of network service providers and cloud services, holding them accountable for meeting SLAs and performance expectations.
Network device monitoring refers to the practice of monitoring and managing the performance, availability, and health of network devices within an IT infrastructure. It involves tracking and analyzing various parameters and metrics of network devices, such as routers, switches, firewalls, load balancers, and wireless access points.
The goal of network device monitoring is to ensure that network devices are functioning optimally, maintaining high availability, and performing according to expected standards. By monitoring network devices, administrators can proactively detect issues, troubleshoot problems, and take necessary actions to maintain a stable and reliable network infrastructure.

Network device monitoring typically involves the following activities:
- Device availability: Monitoring the availability of network devices involves checking if the devices are accessible and responsive. It includes verifying that devices are powered on, connected to the network, and responding to network requests. This ensures that devices are operational and reachable for network communication.
- Performance monitoring: Network device monitoring involves tracking performance metrics such as CPU usagen, memory usage, interface traffic, error rates, and response times. By monitoring these metrics, administrators can identify performance bottlenecks, network capacity limitations, or abnormalities that may impact the overall network performance.
- Health and status monitoring: Monitoring the health and status of network devices involves tracking indicators like device temperature, power supply status, fan speed, and other hardware-specific parameters. It helps identify hardware failures, overheating, or other issues that may affect the stability and reliability of network devices.
- Configuration monitoring: Network device monitoring includes tracking device configurations to ensure that they are aligned with the desired standards and best practices. It involves monitoring configuration changes, detecting unauthorized modifications, and verifying that devices are properly configured to support network services and security requirements.
- Event and log monitoring: Network devices generate logs and events that provide valuable information about their operations and activities. Monitoring these logs helps in identifying errors, warnings, security events, or anomalies that may require attention or further investigation.
- Alerting and notifications: Network device monitoring systems often provide real-time alerting and notification mechanisms. When a monitored device experiences performance issues, failures, or deviations from expected behaviour, administrators are alerted through email, SMS, or other notification methods. This enables prompt response and troubleshooting.
By monitoring network devices, organizations can ensure that their network infrastructure operates efficiently, minimizes downtime, and provides optimal performance for users and applications. It allows administrators to proactively manage network devices, address issues before they escalate, and maintain a robust and reliable network environment.
Obkio is a network performance monitoring tool that focuses on providing insights into network performance between locations or endpoints. It offers active monitoring capabilities with customizable tests, real-time performance metrics, and historical data analysis. Obkio helps identify network bottlenecks, assess network quality, and troubleshoot performance issues.
Network device monitoring tools are essential for managing and ensuring the health and performance of network devices, such as routers, switches, firewalls, and servers.
Real-time Device Health Monitoring:
Businesses can use network device monitoring tools to continuously monitor the health and status of network devices. This includes tracking device uptime, CPU and memory utilization, temperature, power supply status, and other hardware-related metrics in real-time.
Performance Optimization:
Network Device Monitoring tools help organizations identify performance bottlenecks in network devices. By tracking device resource utilization and traffic patterns, businesses can optimize device configurations and resource allocation to ensure efficient operation.
Resource Utilization Monitoring:
These tools assist in tracking the resource consumption of network devices, allowing administrators to detect when devices are nearing capacity. This proactive approach helps avoid device overloads and performance degradation.
Device Configuration Changes:
Monitoring tools can alert administrators to any unauthorized or unexpected changes in device configurations. This is critical for ensuring the security and stability of the network.
Network Device Fault Detection:
Businesses can use monitoring tools to detect faults or errors in network devices, such as dropped packets, interface errors, and hardware failures. Detecting these issues early helps prevent network disruptions.
Bandwidth and Traffic Analysis:
Businesses can monitor network devices to track bandwidth usage and traffic patterns, helping to identify which devices are consuming the most bandwidth and which applications generate the most traffic. This data is valuable for capacity planning and network optimization.
Learn about Network Device Monitoring to easily monitor performance of firewalls, routers & switches to identify problems like high CPU & bandwidth usage.
Learn more

Synthetic network monitoring, also known as synthetic monitoring or active synthetic monitoring, is a type of network monitoring that involves simulating user interactions or network traffic to assess the performance and availability of network services, applications, or endpoints. It is called "synthetic" because it generates artificial or simulated traffic rather than relying on real user interactions.
In synthetic network monitoring, pre-defined test scenarios or transactions are executed on a regular basis from designated monitoring locations or endpoints. These tests simulate various user actions or network activities, such as accessing a website, submitting forms, downloading files, or performing specific transactions within an application.
The purpose of synthetic network monitoring is to proactively measure and evaluate the performance and availability of network services or applications from an end-user perspective. It helps identify potential issues, bottlenecks, or outages before real users are affected. Synthetic monitoring provides insights into network response times, latency, error rates, and other performance metrics.

Synthetic network monitoring offers several key features that contribute to its effectiveness in assessing and optimizing network performance. Here are some key features of synthetic network monitoring:
- Proactive monitoring: Synthetic monitoring enables proactive detection of performance issues by simulating user interactions and transactions. It helps administrators identify potential problems and take corrective actions before users experience any impact.
- End-user experience assessment: By simulating user interactions, synthetic monitoring provides insights into how network services or applications perform from an end-user perspective. It helps evaluate response times, accessibility, and functionality, allowing organizations to ensure a positive user experience.
- Baseline establishment: Synthetic monitoring helps establish performance baselines by continuously measuring and tracking performance metrics. This allows organizations to set benchmarks, compare performance over time, and identify deviations or trends that may require attention.
- Geographic coverage: Synthetic monitoring can be conducted from various monitoring locations or endpoints across different geographic regions. This enables organizations to assess performance from multiple locations, identify regional variances, and optimize network services accordingly.
- Scheduled and on-demand testing: Synthetic monitoring tests can be scheduled to run at regular intervals or triggered on-demand. This flexibility allows administrators to monitor network services proactively or conduct immediate tests during specific events or maintenance activities.
- Alerting and notification: Synthetic monitoring tools generate alerts or notifications when performance thresholds are breached or anomalies are detected. This allows administrators to receive real-time alerts, investigate issues promptly, and take appropriate actions to resolve them.
- Synthetic versus real-user monitoring: Synthetic monitoring complements real-user monitoring (RUM), which captures performance data based on actual user interactions. While RUM provides insights into real-world user experiences, synthetic monitoring allows organizations to simulate and control specific scenarios, ensuring comprehensive performance evaluation.

Obkio is a cloud-based network monitoring tool that offers synthetic monitoring capabilities. It allows businesses to simulate user interactions across their network infrastructure to proactively identify and resolve network issues. With Obkio, you can monitor network performance, latency, packet loss, and bandwidth utilization from multiple locations. It provides insights into network health, helps troubleshoot network problems, and ensures optimal network performance for end-users.
Learn how to use synthetic monitoring to monitor network performance & identify network issues, and the benefits of synthetic traffic over packet capture.
Learn more

Synthetic network monitoring tools are designed to simulate network traffic and user interactions to assess the performance, availability, and reliability of network services and applications.
Application Performance Testing:
Synthetic monitoring tools are valuable for testing the performance of critical applications under controlled conditions. By generating synthetic traffic and measuring response times, businesses can assess how applications perform and identify potential performance bottlenecks.
Service-Level Agreement (SLA) Verification:
Organizations that rely on third-party service providers, such as cloud services or content delivery networks (CDNs), can use synthetic monitoring to verify that service providers meet the terms of their SLAs. This includes checking service availability, response times, and content delivery performance.
Website Availability and Performance Monitoring:
Synthetic monitoring is commonly used to monitor the availability and performance of websites. Businesses can set up synthetic tests to regularly check if their websites are accessible and responsive from different geographic locations. This is crucial for e-commerce, online services, and customer-facing websites.
E-commerce Transaction Monitoring:
For businesses with e-commerce platforms, synthetic monitoring tools can simulate customer interactions by performing end-to-end transactions, such as adding items to a shopping cart, completing a purchase, and checking out. This helps verify that the e-commerce process is functioning correctly and delivers a seamless user experience.
Geographic Load Balancing and Global Content Delivery:
Companies that rely on geographic load balancing or content delivery can use synthetic monitoring to confirm that content and services are distributed effectively across various geographic regions, providing low latency and high performance to users worldwide.
Disaster Recovery and Failover Testing:
Synthetic monitoring can be used to test disaster recovery and failover mechanisms. By simulating network or data center failures, businesses can evaluate the effectiveness of their failover procedures and ensure that critical services are available during disruptions or network disconnections.
Cloud Application Performance Assessment:
For organizations using cloud-based applications and services, synthetic monitoring helps assess the performance and availability of cloud services. It can verify that cloud-hosted applications meet performance expectations and SLAs.
Network Performance Benchmarking:
Businesses can use synthetic monitoring to benchmark their network performance against industry standards or competitors. This helps identify areas for improvement and ensures that the network remains competitive.
Proactive Issue Detection:
Synthetic monitoring tools can proactively simulate user interactions to detect issues before they impact real users. This is particularly valuable for identifying performance problems that may only occur under specific conditions.
SNMP (Simple Network Management Protocol) is a widely used network management protocol for monitoring and managing network devices and systems. It is an application-layer protocol that allows network administrators to collect information from network devices, monitor their performance, and manage them remotely.
SNMP monitoring allows administrators to track important metrics such as network bandwidth utilization, CPU and memory usage, device availability, and error rates. It provides real-time visibility into the network infrastructure, enabling proactive troubleshooting, capacity planning, and performance optimization.
To implement SNMP monitoring, network devices must have SNMP agent software installed, and an SNMP manager application or system is required to collect and analyze the data. There are numerous SNMP-based monitoring tools available that provide comprehensive network monitoring capabilities.
SNMP network monitoring offers several key features that help network administrators effectively manage and monitor their network infrastructure. Here are some of the key features:
- Device Discovery: SNMP network monitoring allows administrators to discover network devices automatically. By scanning the network using SNMP, the monitoring system can identify and add devices to its management inventory. This feature simplifies the process of adding new devices to the monitoring system and ensures comprehensive visibility of the network.
- Performance Monitoring: SNMP enables the monitoring of various performance metrics of network devices. Administrators can track parameters such as CPU utilization, memory usage, network bandwidth utilization, interface status, packet loss, error rates, and more. By monitoring these metrics in real-time, administrators can identify performance bottlenecks, troubleshoot issues, and optimize network performance.
- Fault Detection and Alerting: SNMP network monitoring systems can detect faults and anomalies in the network devices. When a monitored parameter exceeds predefined thresholds or encounters an error condition, the monitoring system generates alerts and notifications. These alerts can be delivered via email, SMS, or other communication channels, enabling administrators to respond promptly to critical network issues.
- Configuration Management: SNMP supports the retrieval and modification of device configurations. Network administrators can use SNMP to access and manage configuration parameters of network devices remotely. This feature allows for centralized configuration management, making it easier to apply changes consistently across multiple devices and ensuring adherence to network standards.
- Historical Data Collection and Analysis: SNMP monitoring systems can collect and store historical data about network performance over time. This data can be analyzed to identify trends, patterns, and anomalies. Historical data analysis helps in capacity planning, performance optimization, and troubleshooting by providing insights into network behavior and identifying long-term trends.
Obkio is a cloud-based network monitoring solution that offers SNMP monitoring capabilities, as well as other features such as network performance testing, VoIP monitoring, and more. With Obkio, you can monitor network devices and applications using SNMP, and get real-time performance metrics to help you optimize your network.

SNMP network monitoring tools are specifically designed for managing and monitoring network devices and infrastructure. Here are a few specific instances or use cases when businesses should use SNMP network monitoring tools:
Network Device Health Monitoring:
SNMP tools allow businesses to monitor the health and status of network devices, including routers, switches, firewalls, and servers. This includes tracking device uptime, CPU and memory utilization, interface status, and hardware conditions in real-time.
Fault Detection and Network Troubleshooting:
SNMP network monitoring tools help identify network faults and issues. When network devices experience problems, SNMP-based monitoring tools provide alerts and real-time data, enabling administrators to troubleshoot and resolve issues promptly.
Network Device Configuration Management:
SNMP tools enable businesses to manage device configurations. Administrators can back up device configurations, deploy updates, and roll back configurations to previous states, ensuring consistent and secure device management.
Resource Utilization Monitoring:
SNMP monitoring tools provide insights into resource utilization, helping administrators understand how devices are using CPU, memory, and network interfaces. This information is crucial for optimizing device performance and preventing resource-related problems.
Bandwidth Utilization Monitoring:
Businesses can use SNMP monitoring tools to track network bandwidth usage and identify network congestion or spikes in traffic. This data is essential for managing and optimizing network capacity.
Inventory and Asset Management:
SNMP-based tools help businesses maintain an up-to-date inventory of network devices, including device details, firmware versions, serial numbers, and warranty information. This is critical for asset management and maintenance planning.
Remote Device Management:
SNMP monitoring tools can be used to remotely manage and configure network devices, reducing the need for on-site visits and improving operational efficiency.
Learn about what SNMP monitoring is & how to use it to monitor performance of networking devices like firewalls, routers, switches and wifi access points.
Learn more

Cloud network monitoring is the practice of monitoring and managing the performance, availability, and security of network resources within a cloud computing environment. It involves the collection, analysis, and reporting of network-related data and metrics to ensure that the network infrastructure and services are operating optimally.
In a cloud environment, network monitoring is particularly important because the network serves as the backbone that connects various cloud components, including virtual machines, containers, storage systems, databases, and other resources. Cloud network monitoring allows organizations to gain visibility into the network infrastructure, detect potential issues or bottlenecks, and take proactive measures to maintain a high level of performance and reliability.

Cloud network monitoring involves monitoring the performance, availability, and security of cloud-based networks, services, and resources. Here are some key features of cloud network monitoring:
- Multi-Cloud Monitoring: Cloud network monitoring tools allow administrators to monitor networks and resources across multiple cloud providers, such as Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), and others. This feature provides centralized visibility into the entire cloud infrastructure, regardless of the cloud service provider being used.
- Real-Time Monitoring: Cloud network monitoring offers real-time monitoring of cloud resources and services. It enables administrators to track critical metrics such as network traffic, bandwidth utilization, latency, response times, and resource usage in real-time. Real-time monitoring allows for the proactive identification of performance issues, service disruptions, or security threats.
- Application Performance Monitoring (APM): Cloud network monitoring often includes APM functionality, which focuses on monitoring the performance and availability of cloud-based applications. APM tools collect data on application response times, transaction throughput, error rates, and other application-specific metrics. This enables administrators to identify application performance issues, troubleshoot bottlenecks, and optimize the end-user experience.
- Security Monitoring: Cloud network monitoring includes security monitoring capabilities to detect and respond to security threats and vulnerabilities. It involves monitoring network traffic for suspicious activities, detecting unauthorized access attempts, and analyzing security logs. Additionally, cloud network monitoring tools can integrate with security information and event management (SIEM) systems to provide a holistic view of security across the cloud infrastructure.
- Historical Data and Analytics: Cloud network monitoring tools store historical data about network and resource performance over time. This data can be analyzed to identify trends, patterns, and anomalies, helping administrators with capacity planning, performance optimization, and troubleshooting. Historical data and analytics provide insights into the long-term behaviour of the cloud infrastructure.
- API Integration: Cloud network monitoring tools often provide APIs (Application Programming Interfaces) for integration with other cloud management and automation systems. This enables administrators to automate monitoring tasks, retrieve monitoring data programmatically, and integrate monitoring with their existing cloud management workflows.
Obkio is a cloud-based network performance monitoring tool that provides end-to-end visibility into network performance and user experience. It offers active network monitoring by simulating network traffic from multiple locations and collecting performance metrics such as latency, packet loss, and throughput. Obkio enables administrators to identify network bottlenecks, troubleshoot performance issues, and proactively monitor network performance in real-time.
Cloud network monitoring tools are specifically designed to monitor the performance, availability, and security of cloud-based infrastructure and services.
Multi-Cloud Management:
Many businesses utilize multiple cloud service providers for various services, such as AWS, Azure, and Google Cloud. Cloud network monitoring tools can provide a centralized view and unified management of resources across multiple cloud platforms, making it easier to monitor and optimize cloud resources.
Application Performance Monitoring in the Cloud:
For applications hosted in the cloud, monitoring tools help assess the performance of these cloud-hosted applications. By measuring response times, latency, and user experience, businesses can ensure that their cloud applications meet performance expectations.
Availability and Uptime Monitoring:
Cloud network monitoring tools track the availability and uptime of cloud services and resources. They provide real-time alerts when cloud services experience network outages or disruptions, allowing businesses to take corrective actions promptly.
Serverless and Function-as-a-Service (FaaS) Monitoring:
For serverless and FaaS architectures, monitoring tools help track function execution times, error rates, and resource utilization, ensuring that serverless applications operate efficiently.
Hybrid Cloud Monitoring:
For businesses that have a hybrid cloud environment with a mix of on-premises and cloud resources, cloud network monitoring tools assist in managing and monitoring both environments. This helps ensure a seamless hybrid cloud operation.
Disaster Recovery and Data Backup:
Cloud network monitoring tools can help monitor the status and performance of disaster recovery and backup processes in the cloud. This ensures that data is protected, and recovery processes can be initiated in case of failure.
Discover the secrets to successful cloud network monitoring! Unleash the power of best practices & optimize performance with Obkio. Read more now!
Learn more

Flow-based network monitoring is a technique used to monitor and analyze network traffic by examining flow data. Network flows represent sequences of packets that share common characteristics, such as source and destination IP addresses, ports, protocol type, and other relevant information. Flow data provides a high-level view of network communication patterns, allowing administrators to gain insights into network performance, identify anomalies, and detect potential security threats.
Flow-based network monitoring complements other network monitoring techniques, such as packet capture-based monitoring. While packet capture provides detailed visibility into individual packets, flow-based monitoring offers a more scalable and efficient approach to monitoring large networks and analyzing traffic patterns. It provides a high-level overview of network behaviour and facilitates efficient network management, performance optimization, and security analysis.


Some key components and features of flow-based network monitoring include:
- Flow Data Collection: Flow data is collected from network devices or dedicated flow monitoring tools. Flow data can be generated by various protocols, such as NetFlow (Cisco), IPFIX (Internet Protocol Flow Information Export), sFlow, or J-Flow (Juniper). These protocols provide information about network flows, including source and destination IP addresses, transport protocol, port numbers, packet and byte counts, and timestamps.
- Flow Exporters and Collectors: Flow-based monitoring requires dedicated flow exporters on network devices that generate and export flow data. The flow data is then collected by flow collectors or flow analyzers, which receive and store the data for analysis and reporting. Flow collectors aggregate and correlate flow data from multiple sources to provide a comprehensive view of network traffic.
- Traffic Analysis: Flow-based network monitoring tools analyze flow data to extract valuable insights. Traffic analysis involves examining flow records to understand network behaviour, identify traffic patterns, measure bandwidth utilization, and detect anomalies. Administrators can use flow-based monitoring to identify top talkers, understand traffic distribution across applications or protocols, and detect abnormal or suspicious traffic patterns.
- Performance Monitoring: Flow-based monitoring helps administrators assess network performance by analyzing flow data. They can measure metrics such as latency, packet loss, jitter, and response times based on flow information. By monitoring flow data, administrators can identify performance bottlenecks, optimize network resources, and troubleshoot network performance issues more effectively.
- Security Analysis: Flow-based network monitoring plays a crucial role in network security. Flow data provides visibility into communication patterns, allowing administrators to identify potential security threats, such as distributed denial-of-service (DDoS) attacks, port scanning, or abnormal traffic behaviour. By analyzing flow data, administrators can detect suspicious activities, monitor traffic to critical systems, and facilitate incident response.
Traffic Analysis and Visibility:
Flow-based monitoring tools provide visibility into network traffic patterns, including source and destination IP addresses, ports, protocols, and data volumes. This information is valuable for understanding how network resources are being used.
Network Traffic Profiling:
Businesses can use flow-based monitoring to profile network traffic by categorizing and summarizing flows based on criteria like source, destination, application, or service. This helps in understanding the nature of traffic on the network and identifying trends.
Capacity Planning:
Flow-based monitoring tools assist in capacity planning by analyzing historical traffic data. Businesses can use this data to project future resource requirements and ensure that the network can support growing demands.
Bandwidth Utilization Monitoring:
These tools provide insights into bandwidth utilization by tracking the volume of traffic associated with different applications, services, or network segments. This data helps in identifying bandwidth hogs and optimizing resource allocation.
Network Performance Analysis:
Flow-based monitoring can help assess network performance by identifying latency, packet loss, and jitter across network paths. Administrators can analyze flow data to identify and troubleshoot performance issues.
Network Traffic Forensics:
Flow data is useful for network traffic forensics in the event of a security incident or data breach. It provides a historical record of network flows, enabling investigators to reconstruct network activities and identify the source of the breach.
Distributed network monitoring is an approach where monitoring capabilities are distributed across multiple locations or systems within a network infrastructure. Instead of relying on a single centralized monitoring system, distributed monitoring allows for the collection and analysis of network data from various points or nodes in the network.
In today's network landscape, distributed network monitoring is becoming more prevalent due to the growing adoption of decentralized network architectures and cloud-based services like SaaS, as well as the rise of modern SD-WAN networks and SASE networks. It is particularly well-suited for remote network monitoring, including remote offices, home offices, and distributed data centers.
Modern Network Performance Monitoring Solutions, such as Obkio Network Performance Monitoring software, recognize the significance of distributed network monitoring and incorporate it into their offerings to align with evolving network infrastructures and the demands of cloud-based applications and services.

Distributed network monitoring offers advantages in terms of redundancy, scalability, proximity to resources, and localized insights. By leveraging a distributed monitoring approach, organizations can enhance network visibility, improve troubleshooting capabilities, optimize performance, and strengthen security across their network infrastructure.
Here are key features of distributed network monitoring:
- Redundancy and Fault Tolerance: By distributing monitoring capabilities across multiple locations or systems, distributed network monitoring provides redundancy and fault tolerance. If one monitoring node or system fails, other nodes can continue monitoring, ensuring that network visibility is maintained. This approach enhances the resilience and availability of the monitoring infrastructure.
- Multiple Monitoring Nodes: Distributed network monitoring involves the deployment of multiple monitoring nodes across the network infrastructure. These nodes can be strategically placed at various locations, including data centers, remote offices, or network edges, to capture and analyze network traffic and performance metrics.
- Scalability: Distributed network monitoring facilitates scalability, especially in large and complex networks. By distributing monitoring tasks across multiple nodes, the monitoring load can be effectively distributed, allowing for better performance and scalability. Additional monitoring nodes can be added as the network expands, ensuring that the monitoring infrastructure can handle the growing demands of the network.
- Proximity to Monitored Resources: Distributed monitoring allows monitoring nodes to be strategically placed closer to the monitored resources. This proximity provides more accurate and detailed monitoring information, as it reduces network latency and minimizes the impact of network bottlenecks. Monitoring nodes can be placed at critical network segments, data centers, or remote locations to capture specific traffic patterns and performance metrics.
- Localized Monitoring and Analysis: Distributed network monitoring enables localized monitoring and analysis of specific network segments or locations. Monitoring nodes can focus on specific regions or network segments, providing more granular insights into local network performance, application behaviour, or security threats. This localized approach helps in troubleshooting localized issues, optimizing performance, and enhancing security at specific network locations.
- Bandwidth Optimization: With distributed monitoring, network traffic and monitoring data can be distributed across different monitoring nodes, reducing the bandwidth requirements on a single monitoring system. Instead of funnelling all the network traffic to a centralized monitoring system, distributed monitoring nodes can process and analyze the data locally, optimizing bandwidth utilization and reducing network congestion.
- Hierarchical Monitoring Architecture: Distributed network monitoring often employs a hierarchical architecture, where multiple monitoring nodes feed data to higher-level aggregation points. This hierarchical approach allows for efficient data collection, aggregation, and correlation across different monitoring layers. It provides a scalable and organized way to manage and analyze monitoring data from distributed nodes.
Obkio is a distributed network performance monitoring tool that specializes in measuring end-to-end network performance from the user's perspective. It uses lightweight software agents deployed on end-user devices or network equipment to gather real-time network data. Obkio provides insights into network latency, packet loss, jitter, and bandwidth utilization, helping administrators troubleshoot network issues and optimize performance.
Distributed network monitoring tools are designed to monitor network performance, security, and availability from multiple geographic locations. They are valuable in various use cases where businesses have distributed networks, remote offices, or a global user base.
Multi-Location Network Monitoring:
Distributed network monitoring tools allow businesses to monitor network performance and availability from multiple locations or branch offices. This is critical for maintaining a consistent user experience and ensuring that remote sites have reliable access to central resources.
Global User Experience Monitoring:
For businesses with a global user base, distributed monitoring tools help assess the user experience from different geographic locations. This enables organizations to identify regional performance variations and ensure that users worldwide receive a satisfactory experience.
Cloud Service and CDN Performance:
Distributed monitoring tools can assess the performance and availability of cloud services and content delivery networks (CDNs) from various locations. This is essential for businesses that rely on third-party services to deliver content or applications to users.
Wide Area Network (WAN) Performance Monitoring:
Distributed network monitoring is valuable for monitoring WAN performance, especially for businesses with remote offices or global network deployments. It helps identify WAN-related issues and optimize WAN performance.
End-to-End Application Performance:
Distributed monitoring tools enable end-to-end application performance testing. Businesses can assess how applications perform from different locations and identify regional bottlenecks that may affect application delivery.
Remote Site Network Health:
For organizations with remote sites or branch offices, distributed monitoring tools help assess the health and performance of network devices at these locations. This is crucial for maintaining remote site connectivity and performance.
Capacity Planning for Global Networks:
Businesses with global networks can use distributed monitoring to plan for capacity and resource allocation. By tracking performance and utilization across regions, organizations can ensure that resources meet demand.
Geographic Content Delivery Assessment:
Distributed monitoring tools are valuable for assessing content delivery performance to different regions. This is important for businesses that deliver content, such as video streaming or software updates, to a global audience.
Third-Party Service Performance Verification:
Distributed monitoring tools help verify that third-party service providers meet SLAs and performance expectations from different geographic locations. This is particularly important for ensuring that third-party services deliver as promised.
Learn about distributed network monitoring and how it’s become necessary to monitor decentralized networks like SD-WAN, SASE, and cloud-based (SaaS) applications.
Learn more

Remote network monitoring refers to the process of monitoring and managing a computer network from a remote location. It involves the use of specialized software tools and technologies to collect and analyze network data, performance metrics, and security events without physically being present at the network's location.
Remote network monitoring allows network administrators or managed service providers (MSPs) to monitor the health, performance, and security of networks, devices, and systems from a centralized location. It enables them to proactively detect and respond to network issues, troubleshoot problems, and ensure the network is running efficiently and securely.
Remote network monitoring enables efficient monitoring, troubleshooting, and management of geographically dispersed networks, providing administrators with the necessary tools to ensure network performance, security, and availability from a remote location.
Here are some key features of remote network monitoring:
- Real-time Monitoring: Remote network monitoring provides real-time visibility into network performance, allowing administrators to monitor the status, availability, and performance of network devices, links, and applications. Real-time monitoring enables quick detection and response to network issues, minimizing downtime and optimizing performance.
- Remote Troubleshooting and Diagnostics: Remote network monitoring allows administrators to perform troubleshooting and diagnostics remotely. They can remotely access network devices, run tests, analyze logs, and diagnose network problems without physically being present at the location. Remote troubleshooting speeds up issue resolution and reduces the need for on-site visits.
- Remote Employee Monitoring: With the increasing prevalence of remote work, organizations must prioritize the productivity and connectivity of their distributed workforce. Remote network monitoring encompasses monitoring individual remote employees' network connectivity and performance. This monitoring enables the identification of issues such as unstable Internet connections or VPN problems, enabling IT teams to promptly assist and minimize disruptions that could affect the productivity of remote workers.
- Performance Metrics and Dashboards: Remote monitoring tools offer performance metrics and customizable dashboards to visualize network data. Administrators can track metrics such as latency, packet loss, bandwidth utilization, and response times to assess the health and performance of the network. Dashboards provide a consolidated view of network status and enable quick identification of performance bottlenecks.
- Device and Link Monitoring: Remote network monitoring includes monitoring of network devices, such as routers, switches, firewalls, and servers, to ensure their availability and performance. It also monitors network links and connections to detect issues such as link failures, high latency, or excessive packet loss. Monitoring device and link status helps administrators proactively address potential network problems.
- Application Performance Monitoring: Remote monitoring tools often include application performance monitoring capabilities. They can track the availability, response times, and usage of critical applications and services. Application performance monitoring helps administrators understand how network performance impacts application delivery and user experience, enabling optimization and troubleshooting.
- Historical Data Analysis: Remote monitoring tools store historical network data, allowing administrators to analyze trends, identify patterns, and perform capacity planning. Historical data analysis provides insights into long-term network performance, and usage trends, and helps predict future resource requirements.
Obkio is a powerful remote network monitoring tool that is known for its user-friendly interface and ease of implementation. This tool provides detailed insights into network performance metrics such as latency, packet loss, and bandwidth utilization, and uses synthetic tests to diagnose performance issues in real-time.
Remote network monitoring tools are essential for businesses that need to monitor and manage network infrastructure and devices located in remote or geographically dispersed locations.
Remote Office/Branch Office (ROBO) Management:
For organizations with remote offices or branch offices, remote network monitoring tools provide visibility into the performance and health of network devices, ensuring that remote locations have reliable connectivity and that issues can be identified and resolved remotely.
WAN Performance Monitoring:
Remote network monitoring is valuable for assessing the performance of wide area networks (WANs) that connect remote locations to central data centers. It helps identify WAN-related issues and optimize performance for remote sites.
Retail Store Network Monitoring:
Retail businesses with multiple store locations can use remote monitoring to track the performance of in-store network devices, point-of-sale (POS) systems, and customer Wi-Fi access. This ensures a seamless shopping experience for customers.
Remote Device Health Monitoring:
Remote network monitoring tools help assess the health and status of network devices, such as routers, switches, and firewalls, at remote locations. This is crucial for maintaining network device reliability and performance.
Distributed Data Centers:
For organizations with data centers in multiple locations, remote monitoring is essential for ensuring the performance, availability, and security of data center infrastructure. It helps prevent data center outages and disruptions.
Remote VPN and Remote Workforce Support:
With the increase in remote work, businesses can use remote monitoring tools to assess the performance of virtual private networks (VPNs) and remote work devices. This ensures that remote employees have reliable connectivity and access to corporate resources.
Remote Site Connectivity Assessment:
Remote network monitoring tools help assess the connectivity and performance of network links and devices at remote sites. This is important for maintaining site-to-site connectivity and optimizing link usage.
Managed Service Provider (MSP) Operations:
MSPs can utilize remote network monitoring tools to monitor and manage the networks of their clients, regardless of the clients' geographic locations. This enables proactive support and issue resolution as MSP are able to identify whether performance issues are happening in the MSP network or client network.
Energy and Environmental Monitoring:
Remote monitoring can be used to assess the energy consumption and environmental conditions of remote network equipment and data centers, ensuring efficient operations and compliance with environmental standards.
Unleash the power of remote network monitoring! Discover the benefits, techniques, and be a network superhero with Obkio. Monitor, optimize, and conquer!
Learn more

Application Performance Monitoring (APM) is a practice that involves monitoring and managing the performance and availability of software applications. It focuses on measuring and optimizing the performance of applications to ensure they meet user expectations and deliver a seamless user experience.
APM for HTTP focuses on monitoring and optimizing the performance of individual HTTP-based transactions and requests. It provides insights into the performance of APIs, web services, and other HTTP-based interactions. This includes measuring response times, throughput, error rates, and resource utilization for each HTTP request. APM for HTTP is especially useful for organizations that heavily rely on web APIs or microservices architectures.
APM for Web goes beyond individual HTTP transactions and focuses on monitoring and optimizing the performance of complete web applications and web pages. It includes monitoring page load times, rendering times, user interactions, and the overall user experience. APM for Web may also include features like browser instrumentation, which collects performance data directly from the user's browser, providing a holistic view of the end-to-end web application performance.

APM typically involves the following key aspects:
- Application Monitoring: APM tools monitor various metrics related to application performance, including response times, throughput, error rates, resource utilization, and transaction times. They collect data from the application's code, infrastructure components, and user interactions to gain insights into its behaviour and performance.
- User Experience Monitoring: APM tools track and analyze user interactions with the application, measuring factors such as page load times, click paths, and transaction completion rates. This helps identify bottlenecks or issues that impact user experience, allowing for targeted optimizations.
- Infrastructure Monitoring: APM solutions monitor the underlying infrastructure components supporting the application, including servers, databases, networks, and third-party services. This provides visibility into how the infrastructure affects application performance and helps identify any infrastructure-related issues that may impact the application.
- Error and Log Monitoring: APM tools capture and analyze error messages and logs generated by the application. This helps detect and diagnose errors, exceptions, and performance degradation within the application code, allowing developers to identify and resolve issues promptly.
- Performance Baselines and Thresholds: APM solutions establish performance baselines and define thresholds for key metrics. When performance deviates from the established norms or exceeds defined thresholds, alerts are generated to notify administrators, allowing them to take proactive measures and address potential issues.
- Transaction Tracing: APM tools offer transaction tracing capabilities, which allow detailed monitoring of individual user transactions as they flow through the application. This provides end-to-end visibility into how different components and services contribute to the overall performance of a transaction, aiding in pinpointing bottlenecks or performance inefficiencies.
- Diagnostics and Troubleshooting: APM tools provide diagnostic capabilities to help troubleshoot performance issues. They enable detailed investigation into the root causes of problems, allowing developers and administrators to identify specific areas that require optimization or fixes.
- Reporting and Analytics: APM solutions generate reports and provide analytics to analyze application performance trends, identify patterns, and gain insights into usage patterns, peak load times, and performance improvements over time. These reports help in capacity planning, identifying areas for optimization, and measuring the impact of performance enhancements.
Discover APM for HTTP URLs: Enhance web app performance, troubleshoot issues & delight users with powerful monitoring solutions.
Learn more

Application performance monitoring tools are essential for ensuring the optimal performance, availability, and reliability of critical applications.
Web Application Monitoring:
Application performance monitoring tools are crucial for monitoring the performance and availability of web applications. This includes e-commerce platforms, customer portals, and web-based services. Monitoring helps identify performance issues, such as slow page load times and transaction failures, to ensure a seamless user experience.
Database Performance Optimization:
Businesses can use these tools to monitor database performance and identify slow queries, database bottlenecks, and resource constraints. This ensures that databases support application performance and deliver timely data retrieval and storage.
Virtual Desktop Infrastructure (VDI) Monitoring:
For organizations deploying VDI solutions, application performance monitoring tools help assess the responsiveness and performance of virtual desktops and applications. This is critical for ensuring a productive remote working environment.
Cloud Service Monitoring:
When businesses use cloud-based applications and services, monitoring tools help assess the performance and availability of cloud resources. This ensures that cloud-hosted applications meet performance expectations and SLAs.
Server and Infrastructure Monitoring:
Application performance monitoring tools are valuable for tracking server and infrastructure performance. They can identify resource utilization issues, configuration problems, and hardware failures that may impact application performance.
IoT Application Monitoring:
For businesses that deploy IoT applications, monitoring tools can track the performance and responsiveness of IoT devices and applications. This ensures that data collection and control processes run smoothly.
Real-time Application Monitoring:
Real-time monitoring tools are used to detect and respond to performance issues as they occur. This allows for proactive issue resolution and minimizes the impact of performance problems on users.
Mobile Application Performance Monitoring:
For businesses with mobile applications, these tools can assess the performance of mobile apps on different devices and operating systems. This ensures a smooth mobile user experience.
Discover the power of Application Performance Monitoring (APM). Optimize your digital presence with APM insights. Explore Obkio's NPM and APM features.
Learn more

Types of Network Monitoring Tools #12: Packet Analyzer Network Monitoring Tools (Network Packet Monitoring Software)
Packet analyzer network monitoring, also known as packet sniffing or packet capturing, is a technique used to monitor and analyze network traffic at the packet level. It involves capturing and examining individual network packets to gain insights into network performance, troubleshoot issues, and identify potential security threats.
Packet analyzers, also called Network Packet Monitoring Software, are tools that capture and decode network packets, allowing network administrators and analysts to analyze the contents of the packets and understand the communication happening on the network. These tools provide detailed information about protocols, source and destination IP addresses, port numbers, packet sizes, and other packet-level attributes.
Packet analyzer network monitoring is a powerful technique for gaining deep visibility into network traffic and understanding how data is transmitted across a network.
Key aspects of packet analyzer network monitoring include:
- Packet Capture: Packet analyzers capture network packets by either monitoring network interfaces in real-time or reading packet capture files. They can capture packets on local networks, specific network segments, or even remotely using tools like remote packet capture (RPCAP) or remote monitoring (RMON).
- Protocol Analysis: Packet analyzers can decode and analyze various network protocols, such as Ethernet, IP, TCP, UDP, HTTP, DNS, and more. They provide insights into how these protocols are being used, detect abnormalities, and identify protocol-specific issues.
- Traffic Analysis: By analyzing captured packets, packet analyzers help monitor network traffic patterns, identify bandwidth usage, and detect network bottlenecks. They can provide statistics on the amount of traffic generated by specific hosts or protocols and help optimize network performance.
- Troubleshooting: Packet analyzers are valuable tools for troubleshooting network issues. They allow network administrators to inspect packet-level details, identify errors, diagnose problems, and pinpoint the source of network-related issues.
- Security Analysis: Packet analyzers can assist in network security analysis by monitoring for suspicious or malicious network traffic. They can detect unauthorized access attempts, analyze packet payloads for potential threats, and aid in network intrusion detection and prevention.
- Performance Optimization: By analyzing packet-level data, packet analyzers help optimize network performance by identifying inefficient or misconfigured network devices, diagnosing latency issues, and providing insights into network traffic patterns.
II. Packet Analyzer Network Monitoring Best Practices: When to Use Packet Analyzer Network Monitoring Tools
Packet analyzer network monitoring tools, often referred to as packet sniffers, are designed to capture and analyze network packets, providing granular visibility into network traffic.
Security Incident Response:
In the event of a security incident or data breach, packet analyzers can be used for forensic analysis. They capture packets to determine the source and scope of a security breach, helping in incident response and remediation.
Malware and Intrusion Detection:
Packet analyzers can detect malware and intrusion attempts by analyzing network traffic for suspicious patterns, signatures, or traffic anomalies. They help identify and respond to security threats in real-time.
Quality of Service (QoS) and VoIP Monitoring:
Packet analyzers are used to assess the quality of service and monitor VoIP traffic QoS for VoIP. They measure latency, jitter, and packet loss in real-time to ensure that voice and video calls maintain high quality.
Wireless Network Troubleshooting:
When dealing with Wi-Fi networks, packet analyzers help identify issues related to signal strength, interference, and connectivity problems. This is crucial for maintaining reliable wireless network performance.
Data Center Traffic Analysis:
For organizations with data centers, packet analyzers help assess traffic patterns and the performance of data center networks, ensuring efficient data transfer and reliability.
Application Behavior Analysis:
Packet analyzers can help assess the behavior of specific applications by analyzing packet flows related to those applications. This is essential for understanding how applications interact with the network.

Network traffic monitoring software is designed to track and analyze the data flowing through a computer network. This software is essential for IT professionals and network administrators to ensure the efficient operation of their network, troubleshoot issues, and maintain network security.
Network traffic monitoring software is a critical component for maintaining network performance, ensuring security, and troubleshooting network issues. It offers real-time and historical data analysis, customizable alerts, and a range of features to help network administrators effectively manage and optimize their network infrastructure.
Network traffic monitoring software often includes features that are specific to passive monitoring and packet analysis, which are not typically found in synthetic or active monitoring tools. These features focus on analyzing actual network traffic as it flows through the network. Here are some specific features:
- Packet Capture and Deep Packet Inspection: Network traffic monitoring software can capture and inspect individual network packets, allowing administrators to view the raw data and analyze the content of packets in detail. This level of visibility is not possible with synthetic or active monitoring.
- Protocol Decoding: These tools can decode and interpret various network protocols, providing insights into how different applications and services communicate on the network. This helps in identifying protocol-specific issues and anomalies.
- Anomaly Detection: Network traffic monitoring software can identify unusual or suspicious patterns in network traffic, which may indicate security threats or network performance issues. This includes detecting anomalies in packet behavior, traffic volume, and communication patterns.
- Flow Analysis: Some monitoring tools use flow-based analysis, such as NetFlow or sFlow, to summarize and aggregate network traffic data. This enables administrators to gain insights into the distribution of traffic, identify top talkers, and monitor trends over time.
- Traffic Profiling: These tools can create profiles of network traffic based on criteria like source, destination, application, and service. This allows administrators to understand the nature of traffic on their network.
- Deep Application Insights: Network monitoring software can provide detailed information about the behavior of specific applications, allowing administrators to monitor application performance, detect issues, and optimize their use.
- Session Analysis: These tools can track and analyze network sessions and connections, providing information about session establishment, duration, and termination. This is crucial for understanding how network services and applications interact.
- SSL/TLS Decryption: Some advanced monitoring software can decrypt and inspect encrypted traffic to identify potential security threats or monitor the performance of encrypted services.
These specific features of network traffic monitoring software are crucial for in-depth analysis, troubleshooting, and security monitoring. They provide insights into the actual behavior of network traffic and help administrators gain a deeper understanding of their network's performance and security posture.
Network traffic monitoring software is essential for a wide range of use cases to ensure the performance, security, and reliability of a business's network infrastructure.
Performance Monitoring:
Network traffic monitoring tools are used to continuously assess network performance. By tracking metrics like bandwidth utilization, latency, packet loss, and jitter, businesses can identify and address performance bottlenecks or anomalies in real-time.
Bandwidth Management:
Network traffic monitoring software helps manage and optimize bandwidth usage. Businesses can identify bandwidth-hungry applications or users and allocate resources effectively to ensure critical applications receive the necessary bandwidth.
Security and Intrusion Detection:
These tools play a crucial role in identifying security threats and intrusions. By monitoring network traffic patterns and behavior, businesses can detect and respond to suspicious activities, such as malware infections, DDoS attacks, and unauthorized access attempts.
Policy Enforcement:
Network traffic monitoring helps enforce access control and security policies. Organizations can ensure that security policies are consistently applied across the network, limiting unauthorized access and data exposure.
Quality of Service (QoS) Management:
QoS is essential for businesses that prioritize specific types of traffic, such as voice and video. Network traffic monitoring software helps manage and enforce QoS policies to ensure a consistent user experience.
Remote Site Monitoring:
For businesses with multiple remote or branch offices, network traffic monitoring can ensure that remote locations have reliable access to central resources and maintain acceptable performance levels.
Vendor and Service Provider Accountability:
These tools allow organizations to monitor the performance of network service providers and cloud services, ensuring that they meet their service-level agreements (SLAs) and performance expectations.
Traffic Analysis and Profiling:
Network traffic monitoring software is used to profile and categorize network traffic by application, user, or device. This information helps businesses understand how network resources are being utilized.
Discover the differences, benefits, and implementation strategies of active network monitoring vs passive network monitoring.
Learn more

Network security monitoring tools (NSM) are essential for identifying and mitigating security threats and incidents within a computer network. These tools help security professionals and network administrators detect and respond to malicious activities and security breaches.
Network security monitoring tools are crucial for safeguarding a network's security. They provide real-time monitoring, detection, and response capabilities to help organizations protect their data and systems from security threats and incidents.
- Packet Capture and Analysis: Network security monitoring tools can capture and analyze network packets to provide detailed visibility into network traffic. This allows for the inspection of packet content, which is crucial for identifying potential security threats and attacks.
- Anomaly Detection: NSM tools can identify abnormal patterns or behaviors in network traffic, such as unusual data transfers, unauthorized access attempts, or deviations from baseline network behavior. Anomaly detection helps in identifying potential security incidents.
- Intrusion Detection System (IDS): Many NSM tools include IDS capabilities to detect known attack signatures and patterns. They alert administrators when they identify traffic that matches known attack profiles.
- Intrusion Prevention System (IPS): Some advanced NSM tools incorporate IPS features, which not only detect but also actively block or mitigate threats by taking predefined actions.
- Network Flow Analysis: Network security monitoring tools can analyze network flows and connections, providing insights into communication patterns, data transfers, and identifying potentially malicious or suspicious connections.
- Forensic Capabilities: NSM tools often provide forensic capabilities, allowing administrators to capture and store historical network data for later analysis and investigation of security incidents.
- Protocol Analysis: NSM tools can dissect and analyze network protocols to identify protocol-specific security issues or vulnerabilities that may be exploited by attackers.
- Behavior Analysis: Network security monitoring tools can monitor the behavior of users, devices, and applications within the network to identify deviations from normal behavior that may indicate a security incident.
- Flow and Log Correlation: NSM tools can correlate network flow data with other log data, including firewall logs, system logs, and user authentication logs, to detect security anomalies and provide a more comprehensive view of network security.
- Threat Intelligence Integration: Many NSM tools integrate with threat intelligence feeds to compare network traffic against known indicators of compromise (IOCs) and detect potential threats based on external threat data.
- Incident Response Support: NSM tools can assist in the incident response process by providing data and insights necessary for investigating and mitigating security incidents.
- Compliance Monitoring: Some NSM tools offer compliance monitoring and reporting features to help organizations adhere to regulatory requirements and security policies.
Network security monitoring tools are crucial for identifying and mitigating security threats and vulnerabilities within a business's network infrastructure.
Intrusion Detection:
Network security monitoring tools help identify and respond to intrusion attempts and unauthorized access. They detect suspicious network traffic patterns, known attack signatures, and anomalies that may indicate a security breach.
Malware Detection:
These tools are used to identify malware infections within the network. By analyzing network traffic, they can detect and alert on suspicious behavior, such as communication with known malicious domains or command and control servers.
Anomaly Detection:
Network security monitoring tools employ anomaly detection techniques to identify abnormal network behavior. This can include unusual spikes in traffic, port scanning, or patterns inconsistent with normal network operations.
Incident Response:
In the event of a security incident, these tools provide real-time monitoring and alerting capabilities to support incident response efforts. They help security teams investigate incidents, contain threats, and remediate affected systems.
Insider Threat Detection:
Network security monitoring helps identify potential insider threats by tracking unusual or unauthorized access to sensitive data or systems within the network.
Data Exfiltration Detection:
Businesses can use these tools to detect data exfiltration attempts, where unauthorized users attempt to steal or transfer sensitive data from the network.
Security Policy Enforcement:
These tools assist in enforcing security policies and access controls across the network. They can ensure that security policies are consistently applied and that unauthorized access is prevented.
Traffic Inspection for Threats:
Network security monitoring tools inspect network traffic for threats, such as known malware, phishing attempts, and zero-day vulnerabilities. They help identify and block malicious traffic in real-time.
Advanced Persistent Threat (APT) Detection:
APTs are stealthy, long-term attacks that often go undetected by traditional security measures. Network security monitoring tools can identify patterns and behaviors associated with APTs and alert security teams to potential threats.
Vulnerability Scanning and Assessment:
These tools can be used to assess the network for vulnerabilities that could be exploited by attackers. They assist in prioritizing patch management efforts and mitigating vulnerabilities.
Real-time Threat Intelligence:
Network security monitoring tools can integrate with threat intelligence feeds to provide real-time updates on emerging threats and indicators of compromise (IOCs).

Network application monitoring tools are designed to track and analyze the performance and behavior of applications running on a computer network. These tools are critical for IT professionals and network administrators to ensure optimal application performance, troubleshoot issues, and deliver a positive user experience.
Network application monitoring tools play a crucial role in ensuring the performance and reliability of applications. They offer real-time monitoring, performance metrics, and deep insights into application behavior, helping administrators detect and resolve issues to deliver a better user experience.
- Real-Time Monitoring: Network application monitoring tools provide real-time visibility into application performance, allowing administrators to track metrics and detect issues as they occur.
- Application Performance Metrics: These tools capture key performance metrics, such as response time, latency, throughput, error rates, and resource utilization, to assess the health and performance of applications.
- User Experience Monitoring: Some tools can monitor the end-user experience by tracking metrics like page load times, transaction success rates, and user interactions to ensure a positive experience for application users.
- Dependency Mapping: Network application monitoring tools can automatically map and visualize the dependencies between various components of an application, including databases, APIs, and external services. This helps administrators understand the impact of component failures on overall application performance.
- Transaction Tracing: They allow administrators to trace individual transactions or requests as they move through various application components, helping identify bottlenecks and performance issues at a granular level.
- Alerting and Notifications: These tools can send network monitoring alerts and notifications when predefined performance thresholds are exceeded or when issues are detected, enabling administrators to respond proactively to problems.
- End-to-End Application Visibility: Network application monitoring tools provide end-to-end visibility into the entire application stack, including frontend, middleware, backend, and databases, to identify performance bottlenecks across the entire application environment.
- Deep Application Insights: They offer in-depth insights into application behavior, including SQL query performance, error details, and code-level analysis, making it easier to diagnose and fix issues.
- Integration with APM (Application Performance Management): Many network application monitoring tools are integrated with APM solutions, providing a comprehensive view of application performance and allowing administrators to drill down into specific issues.
- Resource Usage Monitoring: They can monitor server resource usage, including CPU, memory, and disk space, to identify resource bottlenecks that may affect application performance.
- Multi-Protocol Support: Network application monitoring tools can support various application protocols and technologies, including HTTP, HTTPS, TCP, UDP, and more.
Network application monitoring tools are designed to monitor and optimize the performance and availability of networked applications.
Web Application Performance Monitoring:
Network application monitoring tools help assess the performance and availability of web-based applications. This is crucial for ensuring that web applications, such as e-commerce platforms or customer portals, deliver a seamless user experience.
User Experience Assessment:
These tools provide insights into the end-user experience by monitoring user interactions with applications. They track metrics like response times, page load times, and transaction success rates to ensure that users have a positive experience.
Database Performance Optimization:
Network application monitoring assists in optimizing database performance. It identifies slow queries, database bottlenecks, and resource constraints that can impact application performance.
VoIP and Unified Communications (UC) Monitoring:
For businesses that rely on VoIP and UC systems, monitoring tools track the quality of voice and video calls. They measure latency, jitter, and packet loss to ensure high-quality communication.
Application Response Time Analysis:
Network application monitoring tools assess application response times to identify bottlenecks, latency issues, and performance problems. This helps optimize application delivery.
End-to-End Application Performance Testing:
These tools allow businesses to conduct end-to-end application performance tests, including network load testing and stress testing, to ensure that applications perform well under various conditions.

So now that we’ve gone through a list of some of the most popular and effective types of network monitoring tools, you may be wondering, which do you actually need?
When choosing a network monitoring tool for your business, there are several factors to consider to ensure you select the best fit for your specific needs. Here are some tips to help you make an informed decision:
- Define Your Monitoring Requirements: Start by clearly identifying your monitoring requirements. Consider the size and complexity of your network, the types of devices and applications you need to monitor, the level of visibility and granularity you require, and any specific performance or security metrics you need to track. This will help you narrow down the features and capabilities you need in a network monitoring tool.
- Scalability and Flexibility: Ensure that the network monitoring tool can scale with your business as it grows. Consider whether the tool can handle increasing network traffic, additional devices, and expanding network infrastructure. Look for flexibility in terms of deployment options (on-premises, cloud-based, or hybrid networks), integration with other systems, and support for various network protocols and technologies.
- Real-Time Monitoring and Alerting: Look for a network monitoring tool that provides real-time monitoring capabilities and timely alerts. It should continuously monitor key metrics, such as latency, packet loss, bandwidth utilization, and device availability, and promptly notify you of any performance or security issues. Customizable alerting options, such as email, SMS, or push notifications, can help ensure that you stay informed and can quickly respond to critical incidents.
- Ease of Use and User Interface: Consider the user-friendliness of the network monitoring tool. The user interface should be intuitive, providing easy navigation and a clear presentation of monitoring data and insights. A well-designed dashboard and reporting system can significantly enhance the user experience and simplify the analysis of network performance data.
- Scalable Architecture and Distributed Monitoring: If you have a large or geographically dispersed network, consider a network monitoring tool with a scalable architecture and support for distributed monitoring. This allows you to deploy monitoring agents or probes at various locations to capture and analyze network data locally. Distributed monitoring provides more accurate insights, reduces bandwidth requirements, and enables better visibility into specific network segments or remote sites.
- Integration and Compatibility: Assess the compatibility of the network monitoring tool with your existing network infrastructure, systems, and technologies. Ensure that the tool can integrate with other network management tools, security systems, and reporting platforms you use. Compatibility with industry standards, protocols, and APIs can facilitate seamless integration and data exchange with your existing IT ecosystem.
- Security and Compliance Features: Network monitoring tools should prioritize security and compliance. Look for features such as user access controls, encrypted communication protocols, and support for compliance frameworks (e.g., HIPAA, PCI-DSS). The tool should provide network traffic encryption options, secure storage of monitoring data, and built-in security monitoring capabilities to detect and respond to potential threats.
- Support and Documentation: Consider the level of support provided by the network monitoring tool vendor. Evaluate the availability of technical support, including documentation, user guides, online resources, and community forums. Prompt and knowledgeable support can be crucial when you encounter issues or need assistance with the tool's configuration, troubleshooting, or optimization.
- Cost and Return on Investment (ROI): Evaluate the cost-effectiveness and potential ROI of the network monitoring tool. Consider both the upfront costs (licensing, hardware, implementation) and ongoing expenses (maintenance, support, upgrades). Assess the tool's potential to improve network performance, minimize downtime, enhance security, and optimize resource utilization. Balancing the tool's capabilities with your budget and expected benefits is essential.
- Trial and Evaluation: Whenever possible, take advantage of trial periods or evaluation versions offered by network monitoring tool vendors. This allows you to test the tool's functionalities, assess its performance, and determine if it meets your specific requirements before committing to a purchase.
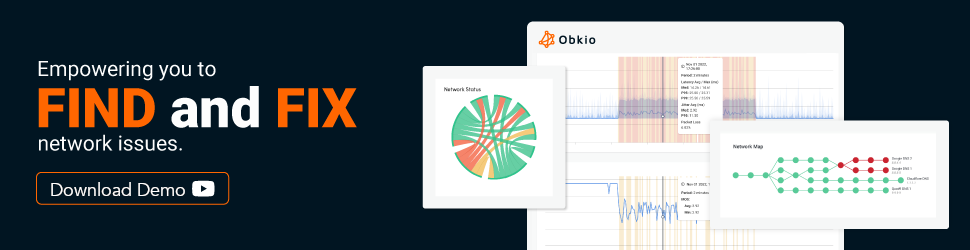

In conclusion, network monitoring tools play a vital role in ensuring the optimal performance, security, and availability of your network infrastructure. By leveraging the right network monitoring tool, you can proactively identify and address potential issues, minimize downtime, and enhance overall network efficiency. To support this further, the best procurement software can help streamline the acquisition and subscription renewals of your chosen tools, ensuring timely updates and cost-effective solutions.
Throughout this guide, we have explored various types of network monitoring tools, each with its own unique set of features and capabilities. From SNMP-based monitoring tools to cloud-based solutions, flow-based monitoring tools, distributed monitoring tools, and remote monitoring options, there is a wide range of options available to suit different network architectures and monitoring requirements.
However, amidst the multitude of choices, one network monitoring tool stands out: Obkio.
With its comprehensive and user-friendly approach to network performance monitoring, Obkio offers a powerful solution for businesses of all sizes. Whether you need to monitor the performance of critical applications, troubleshoot network issues, or ensure seamless connectivity for remote workers, Obkio has you covered.
Take the next step in optimizing your network's performance and try Obkio today. With its advanced features, intuitive interface, and real-time insights, Obkio can empower your IT team to take control of your network's health and drive productivity. Don't wait - unleash the power of Obkio and unlock the true potential of your network.
And experience the difference it can make in revolutionizing your network monitoring journey. Your network superheroes await!
- 14-day free trial of all premium features
- Deploy in just 10 minutes
- Monitor performance in all key network locations
- Measure real-time network metrics
- Identify and troubleshoot live network problems
Click below to try Obkio and elevate your network monitoring game today!

You can rest assured that we're not like those pushy Sellsy people - there's no catch here. We firmly believe in the excellence of our product, but if it's not the right fit for you, we understand and want what's best for you.


























 Obkio Blog
Obkio Blog














